Static analysis of “Heaven’s Gate”
Overview
In the spring of 2020, I obtained and analyzed a sample of malware called “Emotet”. The malware is one of the most violent malware in Japan in 2020. The malware used several techniques that bothered analysts.
In an article I wrote earlier, I introduced the “Function-based encryption” technique. This specimen was also used with another technique called “Heaven’s Gate”.
This article gives an overview of “Heaven’s Gate” and how to do static analysis.
Target malware hash value:
MD5:545BFDC9B1976AE0003443FF4F90EB7E
SHA1:92E8CE006BB3C4A1DDB8D8BA8DE3A90C0BBB6326
Using Debugger:
IDA Pro (Hex-rays)
What is “Heaven’s Gate”?
“Heaven’s Gate” is a technique to run a 64-bit process from a 32-bit process, or a 32-bit process from a 64-bit process. This can be achieved by executing a call or jump instruction using the reserved selector. More detail articles can be found at the links below.
Knockin’ on Heaven’s Gate — Dynamic Processor Mode Switching
http://rce.co/knockin-on-heavens-gate-dynamic-processor-mode-switching/
stack overflow — Switch from 32bit mode to 64 bit (long mode) on 64bit linux
https://stackoverflow.com/questions/24113729/switch-from-32bit-mode-to-64-bit-long-mode-on-64bit-linux
The key points in analyzing this technique are as follows.
- To change the process mode from 32-bit to 64-bit, specify the selector “0x0033” and execute a far call or far jump.
- To change the process mode from 64-bit to 32-bit, specify the selector “0x0023” and execute a far call or far jump.
If you find these instruction executions, you should determine that you have used “Heaven’s Gate”.
Why is this technique used by malware?
It seems that the purpose of malware using this technique is to avoid detailed analysis by the debugger. Also, dynamic analysis of some sandboxes may fail. Debugger analysis runs 32-bit applications as 32-bit processes. However, even if the instruction becomes 64 bits in the middle, it tries to execute in 32 bits. For this reason, the debugger analysis fails. Some sandboxes that emulates the execution of a program will also fail for the same reason. On the other hand, dynamic analysis that runs and monitors processes can be successful.
In fact, I once failed the analysis. I noticed that the instruction changed from 32 bits to 64 bits in the middle. But I didn’t know why it changed because I didn’t know “heaven’s Gate”. Therefore, malware analysts should be aware of this technique.
Static analysis of “Heavens’ Gate”
In this article, I will introduce an example of actually analyzing a specimen. The figure that actually used “Heaven’s Gate” is shown below(Figure 1).

Far call is executed with selector 0x0033 specified at 0x05950006. Codes after 0x05950011 have an unnatural “dec eax”. Because the code after 0x05950011 is 64-bit. However, the debugger analyzes it as 32-bit code, which makes the code strange. The code after 0x10001000 that is called after that is also strange code(Figure 2).

Can we use this debugger to analyze the code correctly? Yes, there is a way. IDA can edit the attributes of the segment. Select “View”-“Open subviews”- “Segments” from the menu. A list of segments is displayed under Program Segmentation. Select the target segment, right-click to display a pop-up message, and click “Edit segment …”. Then, the following dialog will be displayed(Figure 3).

There is “Segment bitness” in the dialog. Set this to “64-bit”. Then click “Analyze selected area” in the pop-up menu to reparse the code after 0x10001000. The result is the correct 64-bit instruction code(Figure 4).

It’s important to note that you must use the 64-bit version of IDA. If you were analyzing with the 32-bit version of IDA, you will need to re-analyze with the 64-bit version. In this case, I also started over. IDA can analyze 32-bit applications in 32-bit, even in the 64-bit version. But I didn’t know how to execute a process running 32 bit on IDA halfway to 64 bit. Perhaps IDA doesn’t have the ability to run as 64-bit in the middle. The code can be read as 64-bit, but it runs as 32-bit and does not work well.
64-bit code extraction
In this case, I could find a way to further analyze. If you analyze the same specimen, with accurate analysis you will be able to discover the decrypted 64-bit code. 64-bit code that I have found are shown below(Figure 5).

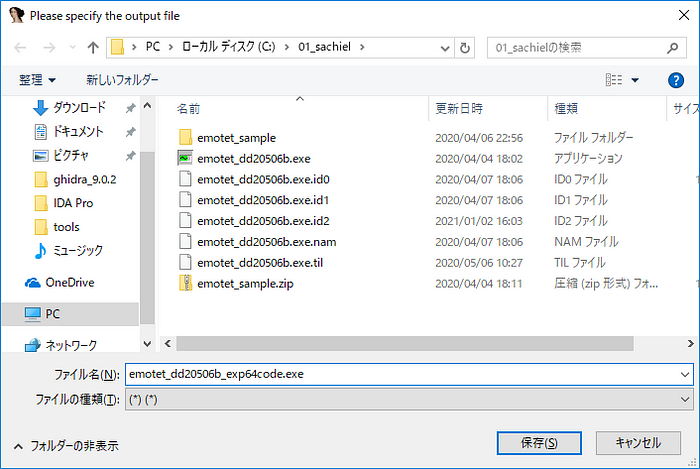
IDA can output this code to a file. Select the output range and right-click to display the pop-up menu. Then click “Save to file …”(Figure 6).

The extension of the file name should be “.exe”(Figure 7). And open the output file in IDA Pro 64-bit version. It can be analyzed correctly with 64 bits(Figure 8).
What’s more, this can be done with a debugger!

Consideration
In this article, I introduced a case where malware uses “Heaven’s Gate”. I specifically presented how 32-bit processes turn into 64-bit processes. I also presented how to display 64-bit code correctly and perform static analysis. If you didn’t know “Heaven’s Gate”, this sample case would be useful for analysis.
The 64-bit code extracted in this case could be executed. Analysis revealed that this 64-bit code was intended to inject and execute code into the “svchost.exe” process created by the 32-bit process.
In part 2, introduces a technique that uses this 64-bit code to inject code into “svchost.exe” created by a 32-bit process and capture thread resumes.
